圖書館:政府监听项目列表
外觀
本文章列舉了世界各國政府已知的監聽計劃和數據庫。
國際項目
[編輯]- 梯隊系統:信號情報(SIGINT)收集和分析網絡,為了五個UKUSA協定簽署國運作。
歐盟
[編輯]- 申根信息系統:出於國家安全和執法目的設立的數據庫。
- {{link-en|INDECT|INDECT}}:歐盟出資支持的研究項目,用於開發在城市環境中監控異常行為的方法(例如處理閉路電視的數據流)。[1]
各國國內項目
[編輯]{{PRC}}
[編輯]{{Main|中華人民共和國大規模監控}}
- 金盾工程:是該國公安部設立的審查和監聽項目,「防火長城」是工程的一個子項目。該項目始於1998年,於2003年開始運作。[2]
- 天網 (中國):是中華人民共和國政府建成的世界上最大的視頻監控系統,利用了人臉識別、大數據、人工智能等技術,是中國大陸大規模監控體系的一部分。[3]天網系統連接不同地方(例如:火車站、飯店、商場、劇院等公共場所,公交、地鐵、出租車等交通工具)的監控鏡頭,可在極短時間內識別大量民眾身分。[4]
- 實時市民運動信息平台:是中華人民共和國北京市科學技術委員會於2011年提出的一款手機位置跟蹤程序,此程序以緩解程式交通流量問題為由跟蹤市民實時位置[5]
- 防火長城:是對中華人民共和國政府在其互聯網邊界審查系統(包括相關行政審查系統)的統稱,主要指中國政府用於過濾互聯網國際出口上內容的軟硬件系統的集合。其主要作用在於分析和過濾中國境外網絡不利於中國政府的資訊互相存取。
- 一體化聯合作戰平台:一款政府和警用應用程式,它常被中國政府用於識別和跟蹤對中華人民共和國新疆地區穩定構成潛在威脅的人員[6][7]
- 五七體制:是中華人民共和國文革時期的體制,該體制下毛澤東的權威達到頂峰,並且民間人們開始互相檢舉以進行思想審查。[8]
- 綠壩·花季護航:是一款客戶端的網絡過濾軟件。該軟件可監控使用者瀏覽的網頁並且過濾特定信息[9],中國大陸當局稱安裝軟件的目的在於保護未成年電腦使用者,也有觀點認為這一軟件是當局進行網絡審查的工具之一。
{{FRA}}
[編輯]
{{IND}}
[編輯]- {{link-en|NATGRID|NATGRID}}:連接印度政府多個部門的數據庫的情報網格系統。
- {{link-en|Centralized Monitoring System|中央監聽系統}} (CMS):類似美國國家安全局的稜鏡計劃的數據收集系統。[11]
- {{link-en|DRDO NETRA|DRDO NETRA}}:與梯隊系統屬同一類型, 使用預定義的過濾規則截取電子郵件, web 論壇消息, 博客, 社交網路, 以及圖像。
{{RUS}}
[編輯]{{SWE}}
[編輯]- {{link-en|巨人通信數據庫|Titan traffic database}}:{{link-en|瑞典國防電信局|Swedish National Defence Radio Establishment}}建立的數據庫,儲存了電話服務的{{link-en|通話詳請記錄|Call detail record}}和互聯網通信內容,以及涉及國際通信的數據庫事務 (transaction) 數據。
{{SWI}}
[編輯]- {{link-en|Onyx|Onyx (interception system)}}:由數個瑞士情報機構維護的數據收集系統。
{{UK}}
[編輯]{{USA}}
[編輯]
- {{link-en|全國可疑行為報告計劃|Nationwide Suspicious Activity Reporting Initiative}}:在該計劃下,執法者、公共安全人員、關鍵基礎設施所有者或一般公眾, 可提出{{link-en|可疑行為報告|Suspicious Activity Report (justice and homeland security}}。
- 稜鏡計劃:由美國國家安全局運作的電子監聽項目,監聽目標是參與該項目的公司的客戶。
- Fairview:由美國國家安全局運作的針對外國移動訂戶的大規模監聽項目。
- X-Keyscore
- {{link-en|DCSNet|DCSNet}}:美國聯邦調查局的監聽項目,可對位於美國境內的任何電信設備實施即時監聽。[13]
- {{link-en|Main Core|Main Core}}:存儲着被認為對美國國家安全構成威脅的美國公民的個人和金融信息的數據庫。[14] 數據多來源於美國國家安全局、美國聯邦調查局、美國中央情報局以及其他政府來源。[14]
- {{link-en|「幻燈」|Magic Lantern (software)}}:鍵盤監聽軟件,由美國聯邦調查局通過電子郵件附件部署;啟用後充當軟件木馬,使聯邦調查局解密用戶通信。[15]
- {{link-en|美國國家安全局通話數據庫|NSA call database}}
- 恆星風
- 641A 室
- 美國情報體系
- 特定入侵行動辦公室:美國國家安全局的情報收集單位,每小時可收集2拍字節的數據。[19][20]
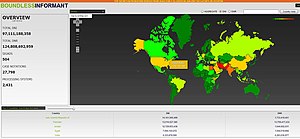
- {{link-en|無界線人|Boundless Informant}}:由於美國國家安全局部署的用於分析全球電子信息的系統。 2013年3月, 該項目收集了分別來自伊朗、印度和美國的 14,000,000,000 份, 6,300,000,000 份, 和 2,800,000,000 份數據報告。[21]
來源不明
[編輯]最近停止運作的項目
[編輯]- {{link-en|恐怖分子監聽計劃|Terrorist Surveillance Program}}:美國的一項監聽計劃,由稜鏡計劃替代。
- {{link-en|ThinThread|ThinThread}}
- {{link-en|Trailblazer 項目|Trailblazer Project}}
- {{link-en|多國反恐信息交換計劃|Multistate Anti-Terrorism Information Exchange}}(MATRIX):最初由{{link-en|佛羅里達執法部門法部|Florida Department of Law Enforcement}}開發的數據挖掘系統。
參見
[編輯]- 大規模監控
- {{link-en|電子警察國家|Electronic police state}}
- 美國國家安全局無證監聽爭議
- {{Link-en|美國國安局全球監控醜聞|Global surveillance disclosures (2013–present)}}
- 政治媒體複合體
參考文獻
[編輯]{{reflist|2}}
Category:情報收集 Category:監視 Category:政府秘密計劃 Category:諜報行動 Category:列表
- ^ Johnston, Ian (19 September 2009). {{Wayback|url=http://www.telegraph.co.uk/news/uknews/6210255/EU-funding-Orwellian-artificial-intelligence-plan-to-monitor-public-for-abnormal-behaviour.html |date=20130810202538 }} {{Wayback|url=http://www.telegraph.co.uk/news/uknews/6210255/EU-funding-Orwellian-artificial-intelligence-plan-to-monitor-public-for-abnormal-behaviour.html |date=20130810202538 }} {{Wayback|url=http://www.telegraph.co.uk/news/uknews/6210255/EU-funding-Orwellian-artificial-intelligence-plan-to-monitor-public-for-abnormal-behaviour.html |date=20130810202538 }} "EU Funding 'Orwellian' Artificial Intelligence Plan to Monitor Public for 'Abnormal Behaviour'{{spaced ndash}} The European Union Is Spending Millions of Pounds Developing 'Orwellian' Technologies Designed to Scour the Internet and CCTV Images for 'Abnormal Behaviour'" {{Wayback|url=http://www.telegraph.co.uk/news/uknews/6210255/EU-funding-Orwellian-artificial-intelligence-plan-to-monitor-public-for-abnormal-behaviour.html |date=20130810202538 }}. The Daily Telegraph. Retrieved 13 June 2013.
- ^ {{cite web|title=How China’s Internet Police Control Speech on the Internet|url=http://www.rfa.org/english/commentaries/china_internet-11242008134108.html%7Cpublisher=自由亞洲電台%7Caccessdate=11 June 2013|quote=China’s police authorities spent the three years between 2003 and 2006 completing the massive 「Golden Shield Project.」 Not only did over 50 percent of China’s policing agencies get on the Internet, there is also an agency called the Public Information Network Security and Monitoring Bureau, which boasts a huge number of technologically advanced and well-equipped network police. These are all the direct products of the Golden Shield Project.|archive-date=2013-07-11|archive-url=https://www.webcitation.org/6I1ZApv1g?url=http://www.rfa.org/english/commentaries/china_internet-11242008134108.html%7Cdead-url=no}}
- ^ {{cite news |author1=陳詩嫻 李貞 |title=「天網」網什麼 |url=http://paper.people.com.cn/rmzk/html/2017-11/20/content_1825998.htm |accessdate=2020-01-19 |work=人民周刊 |agency=人民周刊 |archive-date=2019-03-03 |archive-url=https://web.archive.org/web/20190303234110/http://paper.people.com.cn/rmzk/html/2017-11/20/content_1825998.htm |dead-url=yes }}
- ^ {{cite news |author1=ZOL中關村在線 |title=中國天網已建成 2億攝像頭毫秒級尋人 |url=http://tech.ifeng.com/a/20180504/44980719_0.shtml |accessdate=2020-01-19 |work=鳳凰網 |archive-date=2018-05-04 |archive-url=https://web.archive.org/web/20180504074749/http://tech.ifeng.com/a/20180504/44980719_0.shtml |dead-url=no }}
- ^ {{cite news |author1=Lewis, Leo |title=China mobile phone tracking system attacked as 'Big Brother' surveillance |url=https://www.theaustralian.com.au/news/world/china-mobile-phone-tracking-system-attacked-as-big-brother-surveillance/news-story/7b19fabb97743ea3ba99d36cb1e1c6fa |accessdate=2020-01-19 |work=The Australian |archive-date=2014-06-19 |archive-url=https://web.archive.org/web/20140619132308/http://www.theaustralian.com.au/news/world/china-mobile-phone-tracking-system-attacked-as-big-brother-surveillance/story-e6frg6so-1226015917086 |dead-url=no }}
- ^ {{cite news |author1=Human Right Watch |title=中國的算法暴政 對新疆警方大規模監控APP的逆向工程 |url=https://www.hrw.org/zh-hans/report/2019/05/01/329644 |accessdate=2020-01-19 |work=Human Right Watch |archive-date=2020-01-18 |archive-url=https://web.archive.org/web/20200118172140/https://www.hrw.org/zh-hans/report/2019/05/01/329644 |dead-url=no }}
- ^ {{cite news |author1=Bang Xiao |title=人權觀察揭秘新疆警用APP 36種行為皆可定罪 |url=https://www.abc.net.au/chinese/2019-05-02/chinese-surveillance-app-reverse-engineered-by-rights-group/11071818 |accessdate=2020-01-19 |work=ABC |archive-date=2020-04-13 |archive-url=https://web.archive.org/web/20200413125017/https://www.abc.net.au/chinese/2019-05-02/chinese-surveillance-app-reverse-engineered-by-rights-group/11071818 |dead-url=no }}
- ^ {{cite book |author=錢理群 |title=毛澤東時代和後毛澤東時代(1949-2009): 另一種歷史書寫 |date=2012 |publisher=聯經出版事業股份有限公司 |isbn=9789570839258 |page=86 |edition=初版 |url=https://www.worldcat.org/title/mao-zedong-shi-dai-he-hou-mao-zedong-shi-dai-1949-2009-ling-yi-zhong-li-shi-shu-xie-xia-ce/oclc/1081036436 |accessdate=2020-01-19 |archive-date=2020-04-13 |archive-url=https://web.archive.org/web/20200413125022/https://www.worldcat.org/title/mao-zedong-shi-dai-he-hou-mao-zedong-shi-dai-1949-2009-ling-yi-zhong-li-shi-shu-xie-xia-ce/oclc/1081036436 |dead-url=no }}
- ^ {{cite web |title=綠色上網過濾軟件產品一年使用權及相關服務採購競爭性談判邀請函 |url=http://www.ccgp.gov.cn/cgbx/zybx/2008/604762.shtml |accessdate=2020-01-19 |archive-date=2009-06-16 |archive-url=https://web.archive.org/web/20090616070627/http://www.ccgp.gov.cn/cgbx/zybx/2008/604762.shtml |dead-url=no }}
- ^ {{cite web|title=La France se met à l'espionnage|url=http://reseau.echelon.free.fr/reseau.echelon/espionnage_francais.htm%7Cpublisher=Free (ISP)|accessdate=11 June 2013|language=fr|quote=Frenchelon (ou French Echelon) est le surnom donné au réseau d'écoute de la DGSE. Le véritable nom de ce système d'écoute n'est pas connu (contrairement à ce que nous expliquions, ce n'est pas Emeraude)|archive-date=2013-11-21|archive-url=https://web.archive.org/web/20131121074406/http://reseau.echelon.free.fr/reseau.echelon/espionnage_francais.htm%7Cdead-url=yes}}
- ^ {{cite web|title=India's centralised monitoring system comes under scanner, reckless and irresponsible usage is chilling|url=http://www.dnaindia.com/india/1845205/report-india-s-centralised-monitoring-system-comes-under-scanner-reckless-and-irresponsible-usage-is-chilling%7Cpublisher=Daily News and Analysis|accessdate=12 June 2013|archive-date=2013-07-11|archive-url=https://www.webcitation.org/6I1THu2Hv?url=http://www.dnaindia.com/india/1845205/report-india-s-centralised-monitoring-system-comes-under-scanner-reckless-and-irresponsible-usage-is-chilling%7Cdead-url=no}}
- ^ {{Cite web |url=http://www.theregister.co.uk/2008/10/07/detica_interception_modernisation/ |title=Spy chiefs plot £12bn IT spree for comms überdatabase |accessdate=2013-06-14 |archive-date=2013-06-09 |archive-url=https://web.archive.org/web/20130609165257/http://www.theregister.co.uk/2008/10/07/detica_interception_modernisation/ |dead-url=no }}
- ^ Point, Click ... Eavesdrop: How the FBI Wiretap Net Operates {{Wayback|url=http://www.wired.com/politics/security/news/2007/08/wiretap |date=20100314213702 }}.
- ^ 14.0 14.1 {{citeweb |url=http://www.salon.com/news/feature/2008/07/23/new_churchcomm/ |title=Exposing Bush's historic abuse of power |last=Shorrock |first=Tim |publisher=Salon.com |date=23 July 2008 |accessdate=19 December 2010 |archive-date=2013-07-11 |archive-url=https://www.webcitation.org/6I1ZG2iOt?url=http://www.salon.com/2008/07/23/new_churchcomm/ |dead-url=no }}
- ^ {{cite web |url=http://usgovinfo.about.com/library/weekly/aa121401a.htm |title=FBI Has a Magic Lantern |publisher=Usgovinfo.about.com |date= |accessdate=23 February 2009 |archive-date=2005-05-21 |archive-url=https://web.archive.org/web/20050521022636/http://usgovinfo.about.com/library/weekly/aa121401a.htm |dead-url=no }}
- ^ {{cite news | author = Trenholm, Rich | url = http://crave.cnet.co.uk/gadgets/nsa-to-store-yottabytes-in-utah-data-centre-49304118/ | title = NSA to Store Yottabytes in Utah Data Centre | publisher = CNET | accessdate = 13 June 2013 | archive-url = https://www.webcitation.org/6HpxkQIXk?url=http://crave.cnet.co.uk/gadgets/nsa-to-store-yottabytes-in-utah-data-centre-49304118/ | archive-date = 2013-07-03 | dead-url = yes }}
- ^ {{cite news | title = The NSA Is Building the Country’s Biggest Spy Center (Watch What You Say) | first = James | last = Bamford | authorlink = James Bamford | url = http://www.wired.com/threatlevel/2012/03/ff_nsadatacenter/all/1 | work = Wired | date = 15 March 2012 | accessdate = 5 April 2012 | archive-date = 2013-06-09 | archive-url = https://www.webcitation.org/6HEqAxbOA?url=http://www.wired.com/threatlevel/2012/03/ff_nsadatacenter/all/1 | dead-url = no }}
- ^ {{cite news|url=http://defensesystems.com/Articles/2011/01/07/NSA-spy-cyber-intelligence-data-center-Utah.aspx%7Ctitle=New NSA data center breaks ground on construction -- Defense Systems|last=Kenyon|first=Henry|date=7 January 2011|publisher=Defense Systems|accessdate=11 August 2011|archive-date=2011-10-05|archive-url=https://web.archive.org/web/20111005155823/http://defensesystems.com/Articles/2011/01/07/NSA-spy-cyber-intelligence-data-center-Utah.aspx%7Cdead-url=yes}}
- ^ {{cite web|last=Riley|first=Michael|title=How the U.S. Government Hacks the World|url=http://www.businessweek.com/articles/2013-05-23/how-the-u-dot-s-dot-government-hacks-the-world%7Cwork=Bloomberg Businessweek|accessdate=23 May 2013|date=23 May 2013|archive-date=2013-07-11|archive-url=https://www.webcitation.org/6I1ZE32Is?url=http://www.businessweek.com/articles/2013-05-23/how-the-u-dot-s-dot-government-hacks-the-world%7Cdead-url=no}}
- ^ {{cite book|last=Aid|first=Matthew M.|title=The Secret Sentry: The Untold History of the National Security Agency|url=http://books.google.com/books?id=x_K2rb-OShMC&pg=PA311%7Caccessdate=22 May 2013|date=8 June 2010|publisher=Bloomsbury USA|isbn=978-1-60819-096-6|page=311}}
- ^ {{cite web|title=Meet 'Boundless Informant,' the NSA's Secret Tool for Tracking Global Surveillance Data|url=http://www.theatlantic.com/technology/archive/2013/06/meet-boundless-informant-the-nsas-secret-tool-for-tracking-global-surveillance-data/276686/%7Cpublisher=The Atlantic|accessdate=13 June 2013|quote=The country where the largest amount of intelligence was gathered was, unsurprisingly, Iran: Boundless Informant shows more than 14 billion reports in that period. The second-largest collection came from Pakistan, with 13.5 billion reports. Jordan -- which is, yes, one of America's closest Arab allies -- had 12.7 billion reports. Egypt came in fourth (7.6 billion reports), and India in fifth with 6.3 billion. And when it comes to the U.S.? "The Boundless Informant documents show the agency collecting almost 3 billion pieces of intelligence from US computer networks over a 30-day period ending in March 2013."|archive-date=2013-07-11|archive-url=https://www.webcitation.org/6I1ZEvWKW?url=http://www.theatlantic.com/technology/archive/2013/06/meet-boundless-informant-the-nsas-secret-tool-for-tracking-global-surveillance-data/276686/%7Cdead-url=no}}
- ^ {{cite web |url=http://www.computerworld.com/s/article/print/9185419/Siemens_Stuxnet_worm_hit_industrial_systems?taxonomyName=Network+Security&taxonomyId=142 |author=Robert McMillan |date=16 September 2010 |publisher=Computerworld |accessdate=16 September 2010 |title=Siemens: Stuxnet worm hit industrial systems |deadurl=yes |archiveurl=https://archive.today/20120525053210/http://www.computerworld.com/s/article/print/9185419/Siemens_Stuxnet_worm_hit_industrial_systems?taxonomyName=Network+Security&taxonomyId=142 |archivedate=2012年5月25日 }}
- ^ {{cite web|title=Stuxnet was work of U.S. and Israeli experts, officials say|url=http://articles.washingtonpost.com/2012-06-01/world/35459494_1_nuclear-program-stuxnet-senior-iranian-officials%7Cpublisher=The Washington Post|accessdate=11 June 2013|quote=The officials, speaking on the condition of anonymity to describe the classified effort code-named Olympic Games, said it was first developed during the George W. Bush administration and was geared toward damaging Iran’s nuclear capability gradually while sowing confusion among Iranian scientists about the cause of mishaps at a nuclear plant.|archive-date=2013-05-10|archive-url=https://web.archive.org/web/20130510193607/http://articles.washingtonpost.com/2012-06-01/world/35459494_1_nuclear-program-stuxnet-senior-iranian-officials%7Cdead-url=no}}
- ^ {{cite news | title=Vast Spy System Loots Computers in 103 Countries | url=http://www.nytimes.com/2009/03/29/technology/29spy.html | work=The New York Times | date=28 March 2009 | accessdate=29 March 2009 | author={{tsl|en|John Markoff|Markoff, John}} | archive-date=2009-04-01 | archive-url=https://web.archive.org/web/20090401224950/http://www.nytimes.com/2009/03/29/technology/29spy.html | dead-url=no }}
